With a greater desire for the flexibility that remote working enables taking place around the globe, IT departments are required to ensure hardware and solutions are deployed in such a way that will enable organisations, just like yours, to become more agile and to allow employees to work from home, securely and successfully.
As well as the option of investing in hardware, organisations are looking to “Bring Your Own Device” (BYOD) solutions as an alternative option.
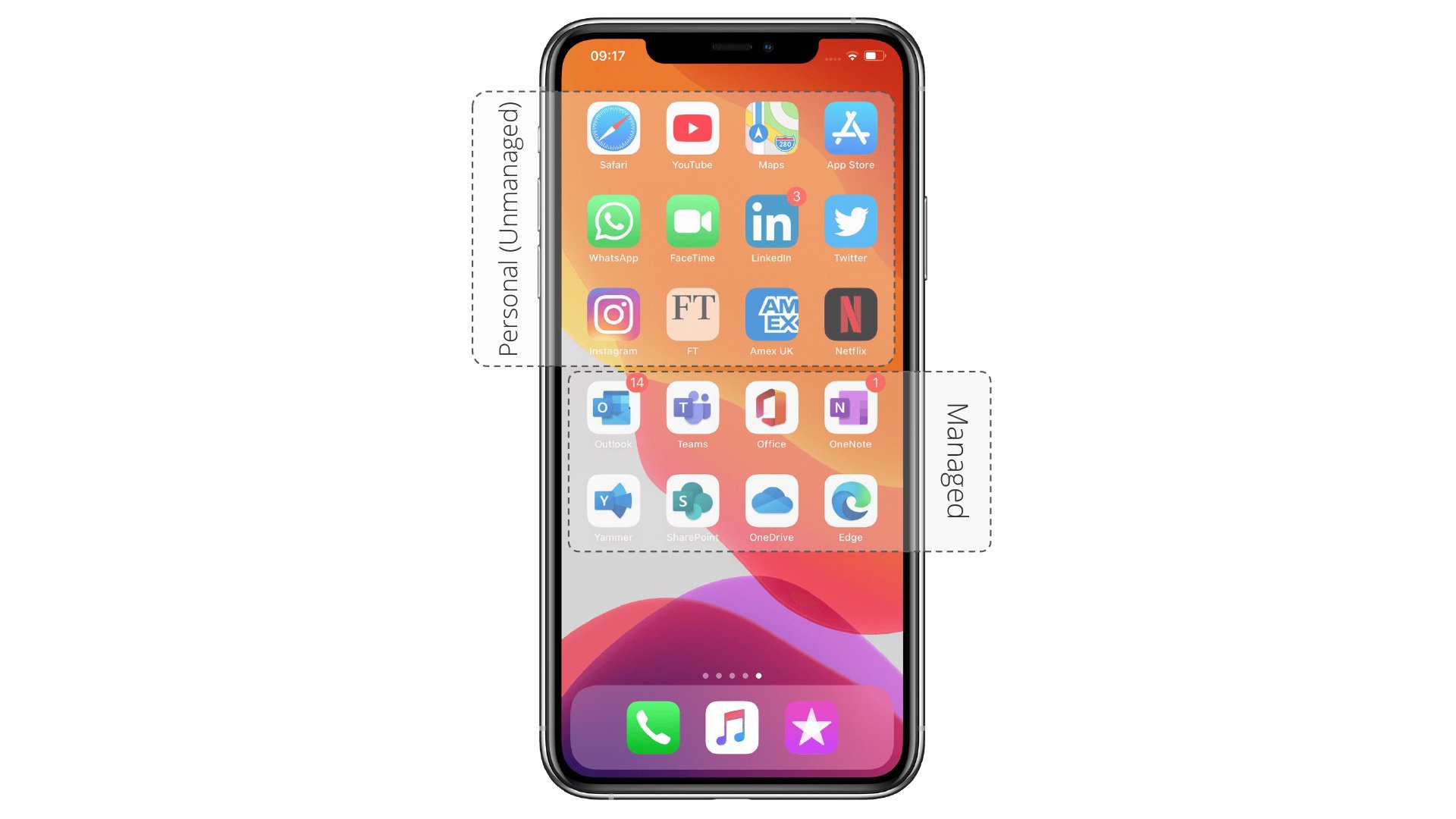
Security and BYOD: Mobile Application Management (MAM)
Where BYOD can solve one issue, it brings with it its own complications and concerns for the security of organisational data.
There is a solution built into Microsoft Intune that can help businesses to extend their perimeter network to include all BYOD devices. Where Mobile Device Management (MDM) works on a device level, Mobile Application Management works on the application and Identity level and allows organisations to deploy security policies to protect corporate data on unmanaged devices.
Application Management is deployed by defining Operating System specific policies to encrypt and protect corporate data whilst being accessed from unmanaged or even managed devices.
These policies allow organisations to define where corporate data can be stored, which applications data can be copied and pasted to, and which sites are included in the organisation’s perimeter network, such as SharePoint Online, an on-premises SharePoint Farm or a file share server.
When a user signs into one of the applications supported by an application management policy, the policy is downloaded to the device and applied to the application, and so ensuring that the organisational data is protected.
Another major benefit of deploying Application Management to unmanaged devices is the ability to remotely wipe organisation data from an end user’s unmanaged device. So, if an end user has lost their phone, the organisation’s IT Admin no longer needs to ask the user to remotely wipe their device. From the Microsoft Endpoint Manager portal (https://devicemanagement.microsoft.com), the organisation can selectively wipe corporate data from applications on a device. This will leave all personal data intact should the device be found again. If the device is found, when the user opens one of the managed applications, they will simply need to reauthenticate and all data will be restored.
iOS and Android Experience
The image below shows how MAM without enrolment works:
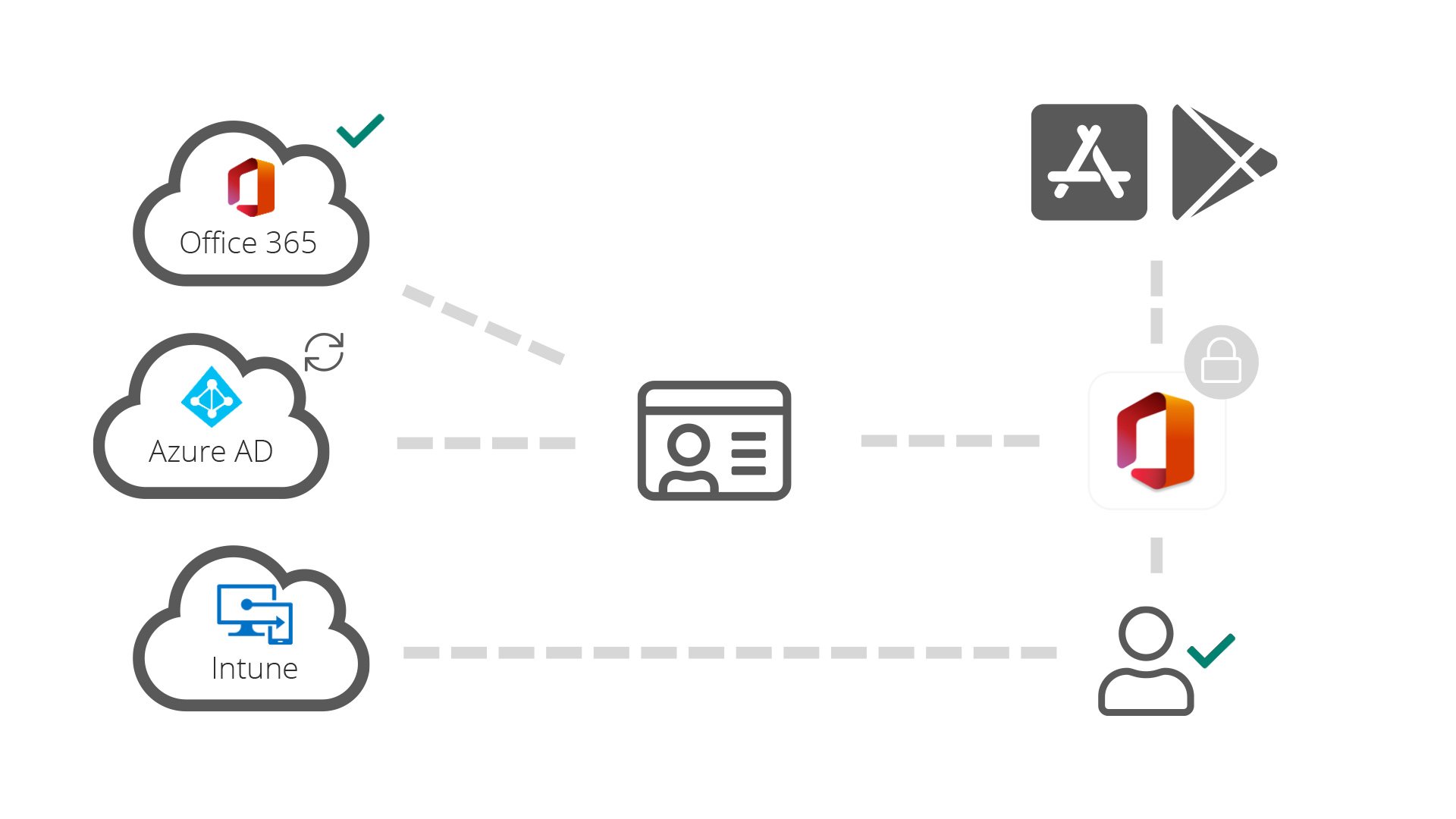
- User installs application from Apple Store or Google Play
- User logs in with Office 365 credentials
- Azure AD verifies that the app and user are allowed access to Office 365
- Intune applies Application Management policies to the managed app
- Access to Office 365 is granted
- User continues to use the app as per usual
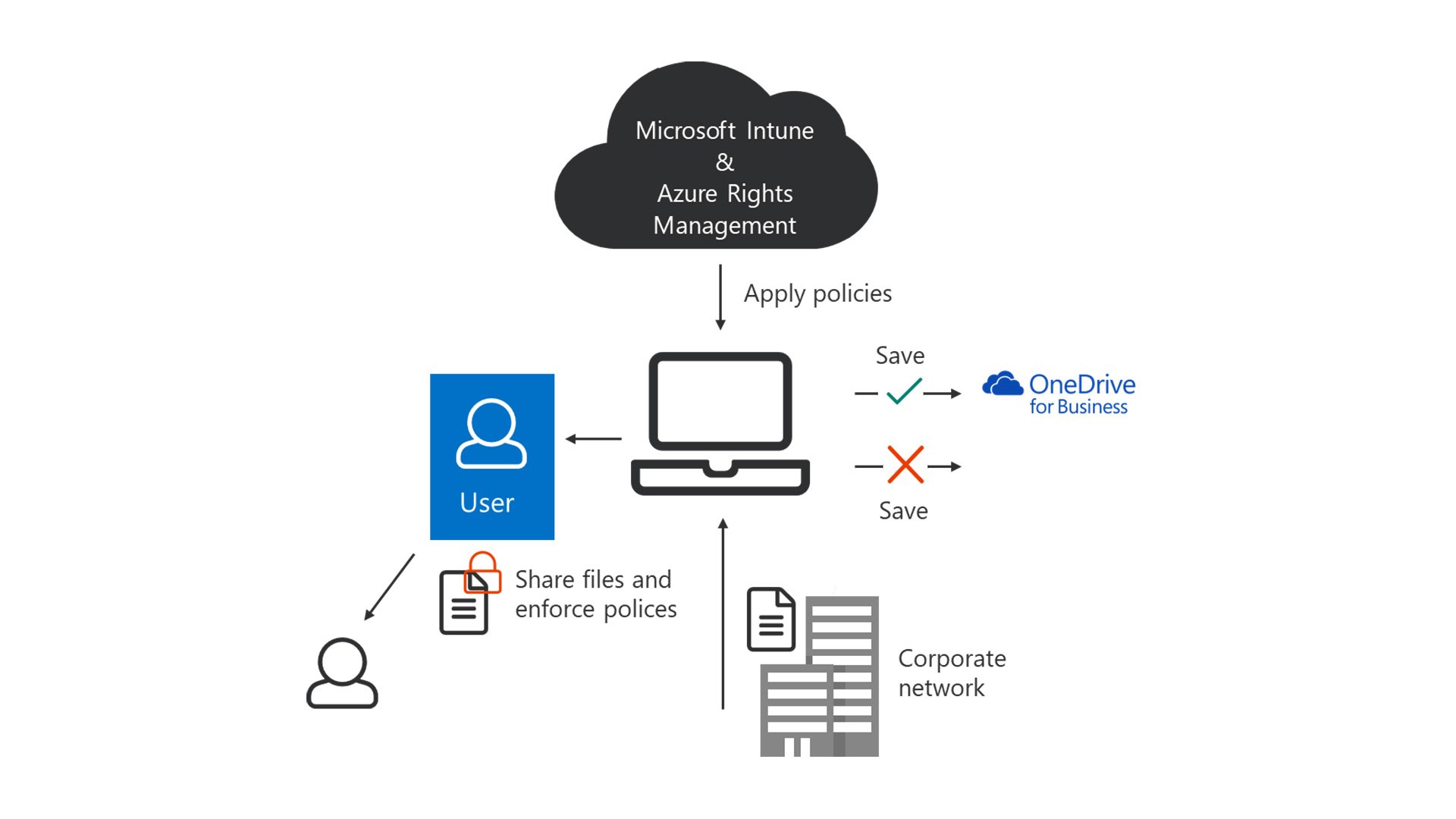
Windows 10
Application Management policies for Windows 10 come under the name of Windows Information Protection, but they deliver the same level of protection. The image below shows the protection for Windows 10.
Key Points
Application Management offers the following security for managed or unmanaged devices:
- App Encryption at rest
- App Access control – pin, biometric or credentials
- Save as / copy / paste restrictions
- App-level selective wipe
- Segregation of corporate and personal data on a user’s personal device
FAQ
Q: What about my corporate devices?
A: Application Management can protect them too. Within Microsoft Intune an organisation can create different policies for managed and unmanaged devices. Alternatively, a policy can be created that applies to both scenarios, ensuring that organisational data receives the same level of protection at the application layer.
Q: I don’t use Intune as an MDM?
A: This is not a problem, MDM management by Intune or a third-party is optional.
Q: Is there any documentation available?
A: Yes plenty, you can find all of Microsoft’s Application Management documentation here: https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/
