The P Word
As with all of you, at the beginning of the ‘P’andemic we at Perspicuity had to move to home working to do our bit to help slow the spread of COVID-19. Several months down the road and it is clear to see that this will not be changing anytime soon.
We have been working with you to help meet some of the massive challenges in the effort to move your colleagues to home working and help you to implement new processes and systems to allow colleagues to access critical line of business applications and data and enable them to be as productive as possible.
Brad Anderson, Corporate Vice President at Microsoft, at the Ignite 2020 conference echoed what we have been witnessing and involved with, in that businesses have had to execute several years of strategies in a matter of months to enable their colleagues to continue to be productive.
Jared Spataro, Corporate Vice President at Microsoft, spoke about the future of work and how the level of change that is being experienced is marking the end of the post-Industrial era, and we are at the dawn of a new era. An era for the digitisation of everything. We are now experiencing a year’s growth in technology every month. Vendors scramble to improve services to meet the new demand and requirements on how they need to service their customers and to improve the end user experience.
Jared Spataro presenting 'The Future of Work' at Ignite 2020
At the beginning of the ‘P’andemic we saw a mass move to Microsoft Teams as organisations shifted to remote working. Discussions have now moved to the deployment of stronger security, driven by the concepts and methodology of Zero Trust, to protect end user identities and corporate data from potential attacks. We have also seen an increase in the amount of businesses that are exploring different deployment models for devices. These have included utilising Windows AutoPilot to allow devices to be shipped directly to the user and configured remotely by Endpoint Manager; no need for IT to touch the device. Windows Virtual Desktop has seen a massive increase in deployments because IT Teams could deploy thousands of new desktops directly into Microsoft Azure, making corporate data and applications accessible through a secure platform from any device.
For me, the Ignite conference really vocalised everything that we have been seeing with our partners, clients and of course with ourselves, and acknowledged the level of changes that needed to happen to enable us to work in the ways we are today. It really demonstrated how the world has embraced home working and all the latest innovations from Microsoft and their partners that are set to really help to accelerate further adoptions of new security strategies and governance, and to make it easier for IT teams to keep on top of the rapid advancements in the way we need to work.
This is also a great opportunity to evolve our way of thinking, living, and interacting with others, either in business or personally. Now is our chance to capture all the ideas of how things could be and to eradicate the phrase “This is how we have always done it”.
Identity and Access
It is very clear that the way in which organisations view technology and how their employees can work has had to completely morph into something new. Cloud based delivery for Identity and authentication is growing exponentially in the scramble to allow colleagues to continue to be productive in a world that is continuously changing.
Microsoft announced at Ignite that they are focusing on the four key areas, when speaking about Identity and Access management:
- Secure Adaptive Access – protect resources and data
- Seamless user experience – keep users productive
- Unified identity management – keep all colleagues connected to apps and data
- Simplified identity governance – automate access controls across hybrid environments
Zero Trust
The message was made very clear from Microsoft during ignite that deploying a Zero Trust methodology for identity and access management to your tenant is the recommended approach. It provides greater security insights across all resources and the introduction of intelligent access policies based on real time risk assessment will provide your security teams the means to protect their colleagues and organisation.
As Conditional Access is at the core of Zero Trust, Microsoft have now introduced insights and recommendations that will now allow you to get the most out of the service and aid in addressing gaps in your Conditional Access Policies.
Identity Secure Score Dashboard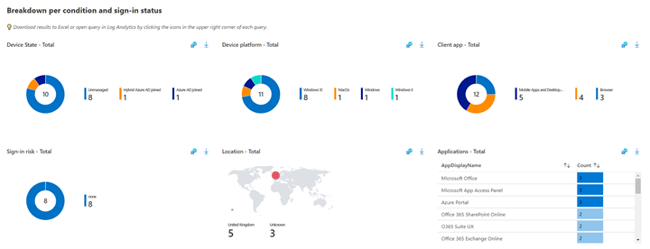
Conditional Access now blocks insecure protocols by default ensuring that the vulnerabilities that come from these legacy methods are handled without any additional configuration and will ensure that all connections to your tenant are being secured. To reduce the risk of implementing new Conditional Access policies to your environment, all new policies will be created in report only mode by default.
One of the significant announcements that came from Ignite was that Conditional Access can now be deployed, maintained, and automated with the new Conditional Access API in Microsoft Graph. Utilising the templates that are now available, you can administer your Conditional Access polices through OneDrive. Once the template is loaded into OneDrive, the new policy is approved through a notification in Microsoft Teams by an admin.
You can explore more information on Zero Trust from Microsoft through the Zero Trust site starting with "Why Zero Trust?"
If you wish to explore Zero Trust and want to discuss deploying this security model to your tenancy, you can find more information on who we can help from our website.
Azure AD Identity Protection
Azure AD Identity protection has had some improvements to help protect your organisation's identities in the Microsoft Cloud.
Improvements have been made to the Password Spray detection and improved the algorithms and they now use a supervised machine learning model which examines over 300 aspects of each authentication request including IP Reputation and behaviour.
Microsoft are catching over 80 Million attacks every day with 98% precision and the system is automatically adapting to new attacks. With better and more accurate detection of attacks like Password Spray, this increases the efficiency of the User Risk policies and will ensure your colleagues are only being prompted for additional authentication information or to change their password when absolutely required.
Your colleagues can help improve the system as Microsoft have given them access to a button to report unauthorised sign ins to their accounts, should someone get passed your Conditional Access policies, within the My Sign Ins” portals at: https://mysignins.microsoft.com
Secure App Eco System
Your colleagues are using new applications to enable them to be productive in the new way of working. App consent settings allows your colleagues to consent to all verified apps, of which there are already over 650 verified publishers, that only need basic user info.
If an app needs more than basic information, then the app will require administrative authorisation before it will be approved.
A big step forward in securing your organisations identity is to ensure that you have single sign on to all applications. That means that all line of business apps need to be integrated into Azure AD.
This has been difficult for some on-premises legacy applications, that require Header-based authentication, which is the most popular type of legacy authentication. The Azure AD Application proxy will soon support this method of authentication. This will allow you to include these legacy applications in the same Conditional Access policies you are currently using for modern authentication applications.
Azure AD Authentication Diagram
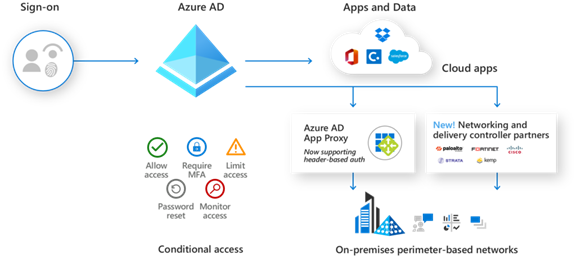
With your legacy applications integrated into Azure AD, using the Azure Application Proxy, and secured by Conditional Access, you will be providing your colleagues with the ability to access the line of business applications they need to be productive from anywhere, whilst ensuring that they are following your security conditions for access, keeping your organisation's data secured.
