IT in business has been moving forward at an extremely fast pace, especially the cloud. The possibilities to enhance users’ experience in your business with innovative new ways of collaboration and new technologies to complement this is exciting!
The Modern Workplace is designed to enhance people and productivity. BYOD (Bring Your Own Device) has become a more popular model for businesses than ever before, and the cloud enables users to access data from anywhere in the world from any device.
However – companies are, rightfully, becoming increasingly conscious of security within the cloud and how to keep their environments and data secure. By adopting a Zero Trust security posture, you can be confident that your cloud environment’s security exceeds your on-premises environment.
Modern problems require modern solutions!
Zero Trust is a phrase that has been gaining traction around the IT industry lately – what does it mean?
Zero Trust is a security strategy. The main premise flips on its head the security that used to work in the old world.
In the old world, all your data and users were under one roof and it was a lot easier to keep your environment secure. You could block out potential attackers with the use of firewalls, but for the most part anything that was on your network was considered trusted.
In the Modern Workplace, where users work in more flexible ways than behind your firewall, these old methods do not work and so with Zero Trust, we start from a viewpoint that nothing is secure and from there, start opening your environment only to users, and apps that are completely trusted.
Although Zero Trust is a strategy and not a feature, Microsoft have this in mind and the Microsoft 365 technology and features available make achieving this Zero Trust model extremely manageable.
Three of the main principles of this strategy are:
Authentication should always be checked based on all the most up to date, available data points, including:
Access to resources should be by exception and not by default. i.e. no resources can be accessed unless user, applications and devices meet your security criteria.
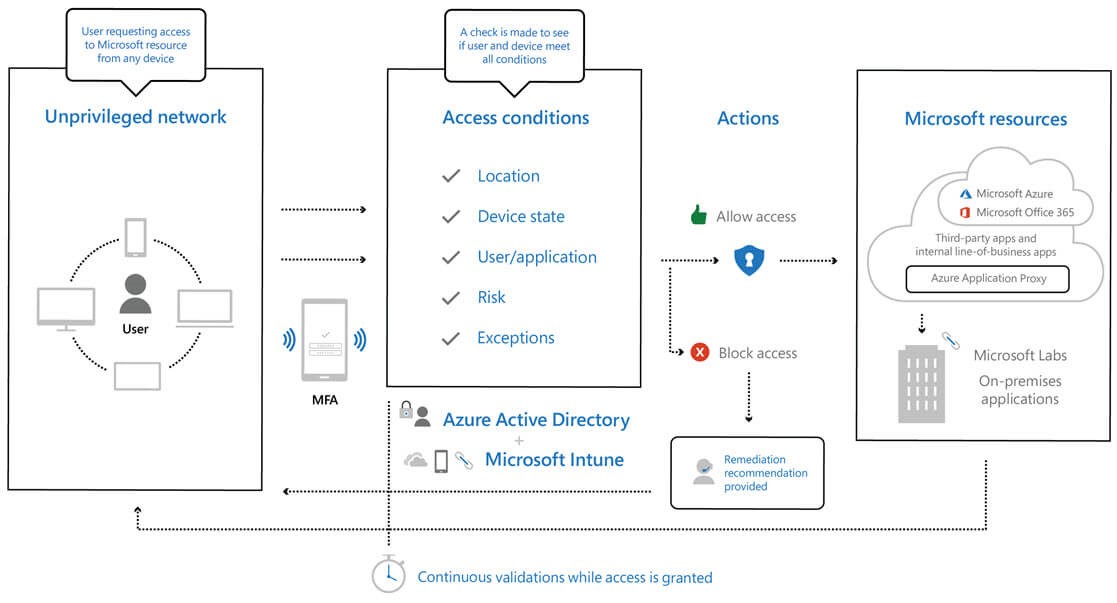
Source: Implementing a Zero Trust security model at Microsoft
A lot of security features available within Microsoft 365 can be used in order to achieve the above. With Conditional Access being the main technology to achieve this, it can be improved to use all the available data points by pulling in other technology such as:
One ideology that isn’t new to IT is limiting user access with just-in-time and just-enough-access (JIT/JEA). Not only this, but also risk-based adaptive policies, and data protection, can be used to secure both data and productivity.
Although the thinking in this space isn’t new, once again there is technology available in Microsoft 365 to achieve this more easily and better than ever before. Some examples are as follows:
By assuming there will be a breach – you will be more prepared if it were to ever happen.
The impact of a breach can be minimised, and lateral movement prevented, by segmenting access by network, user, device, and app awareness. All sessions should be verified and encrypted end to end. Analytics can be used to gain visibility and drive threat detection and improve defences.
Overall, the Modern Workplace is great for business as it improves collaboration, mobility, productivity and end user experience but as described, it brings with it new security threats.
Although securing your Modern Workplace environment is harder than ever before, the suite of tools available in Microsoft 365 are making it easier. By taking a zero-trust approach as described above and leveraging all the available tools and features available with Microsoft 365 – you will find that you are more secure and productive in this new world than you ever were before!
 Ryan Adams | Senior Technical Specialist
Ryan Adams | Senior Technical Specialist
Originally posted 28th February 2020