Microsoft Intune, in Microsoft's own words, is a cloud-based service that focuses on Mobile Device Management (MDM) and Mobile Application Management (MAM). This service is part of the Enterprise Mobility + Security (EMS) suite which makes up a big part of Microsoft 365, integrating directly with other Azure services to improve security and functionality on your organisation's devices.
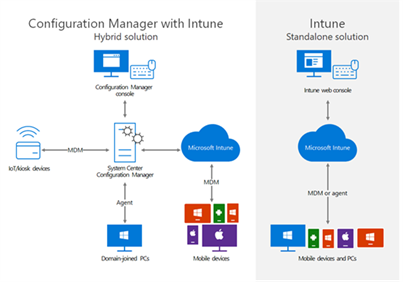
You may have heard of Microsoft Endpoint Manager. Endpoint Manager is Microsoft’s all-encompassing solution to Device management and security. Intune is one of the cloud based technologies that make up part of this solution. Also included within Endpoint Manager is System Centre Configuration Manager (SCCM), which focuses on the on-premises side of device management. One of the biggest benefits to Endpoint Manager including both Intune and SCCM technologies is the ability to co-manage devices in a Hybrid scenario, using the best of both of these technologies to support your transition to the cloud.
Intune allows you to enrol your corporate devices so that you can control, manage, and secure your organisation's devices and applications using a host of policies and controls.
Some of the most notable features and uses of Microsoft Intune you can expect that will help improve your organisation’s device stance:
Intune gives you the ability improve and simplify your device deployment experience. For Windows, you can take advantage of the Autopilot service which allows you to prepare all the relevant policies for users ahead of time and have brand new devices shipped directly to end users, when they sign in, the device will automatically apply all the relevant configuration and apps for that user / device!
For Android and Apple devices, you can use Zero Touch Deployment to achieve a similar scenario by linking Intune with Samsung Knox and Apple Business Manager respectively.
With Intune, you can package and deploy apps directly to end-user devices via the cloud.
Microsoft have created Security Baselines which are available within Intune. The security baselines, which include Windows, Edge, and Defender for Endpoint, is a group of Microsoft-recommended configuration settings designed to give a base protection for your devices.
These settings are based on feedback from Microsoft security engineering teams, product groups, partners, and customers.
Configuration and Compliance policies allow you to tailor your devices in a way that suit your specific organisational needs. Configuration profiles allow you to enforce changes on devices and compliance policies let you ensure the devices are following your organisations policies
With Intune, you can extend your protection from the MDM policies above with the use of MAM policies which allow you to put extra security controls in place to protect organisation data at the application level. This can be particularly useful in BYOD (bring your own device) scenarios where your end-users need to use personal devices to access and process your organisational data.
App protection policies allow you to isolate your corporate data from personal data, giving greater control in securing it. These policies allow you to restrict actions and access based on certain criteria and can get as granular as preventing screenshotting, copy/pasting, and saving/viewing corporate data outside of specifically approved applications.
Check out this video by Microsoft to learn more about MAM
In a future article we go more in-depth about the considerations you should make when moving to Intune from another MDM.
When starting to work with Microsoft Intune on any device platform, we always recommend running a proof-of-concept (PoC) project to ensure your specific needs can be met. If you are interested in talking about this in further detail, please feel free to get in touch!
 Ryan Adams | Senior Technical Specialist
Ryan Adams | Senior Technical Specialist
Originally posted 28th January 2022