As we discussed in our blog post 'Identity and Access Announcements from Ignite 2020', the pandemic has forced organisations to look differently about the common ways in which we work. It has also made organisations think differently about their security to Microsoft 365 and their own on-premises networks.
Organisations are embracing this new Hybrid work era and discovering that users need more flexibility in the way they work, learn, and collaborate with their colleagues and customers. Our customers have been implementing our Zero Trust Identity approach to allow them to achieve maximum security with minimum impact on their colleagues and thus providing them with the flexibility that they need.
Ignite this year had some key announcements to support the continued development of the Zero Trust model and we have summarised some of these below.
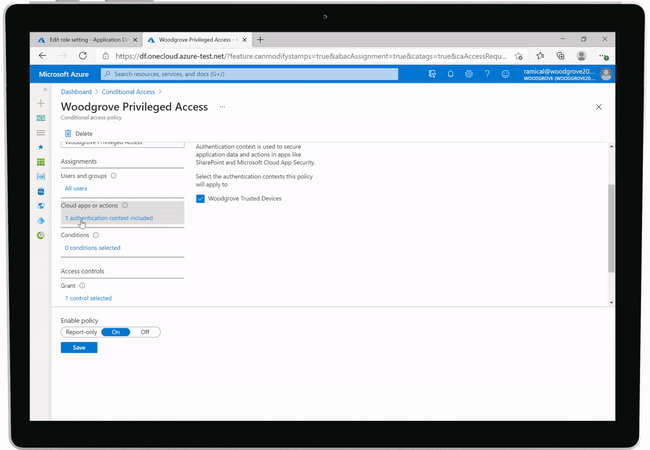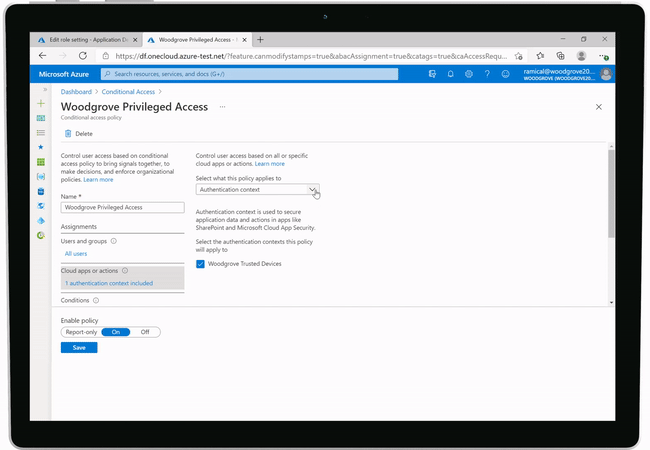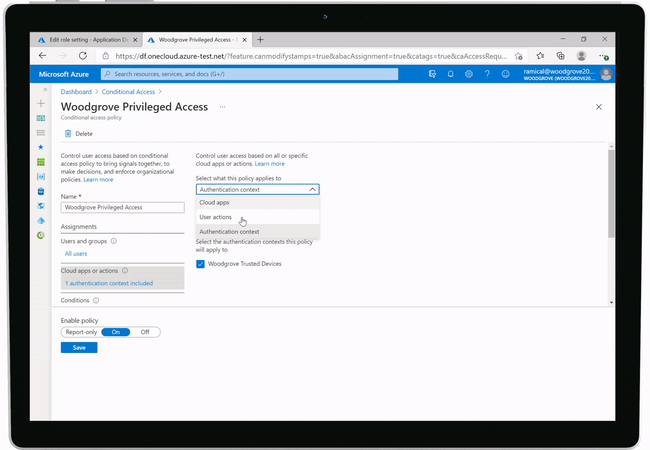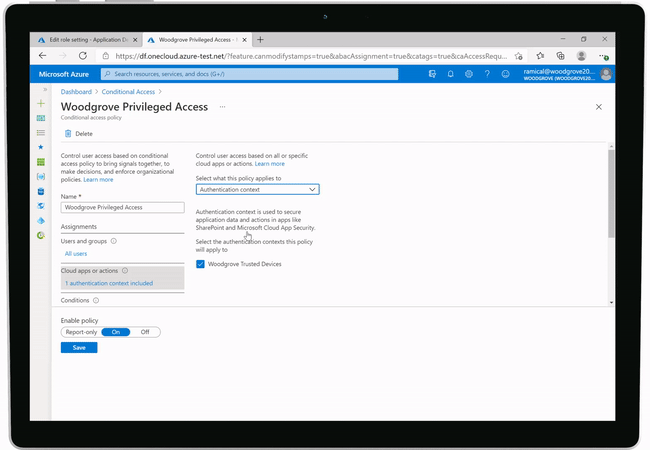
This feature will soon be launched into Azure AD as a preview feature. Once launched it will provide more granular control within Conditional Access (‘CA’) policies and focus on the user interactions and the sensitivity of the data that they are trying to access.
The example that Microsoft gave for this was, that you will be able to create a CA policy that allows a user to access the company banking app, that has been integrated into Azure AD for authentication, from a personal device to manage non-sensitive tasks. If the same user, then needs to perform a more sensitive task, like perform a wire transfer, this action would need to be performed from a corporate device.
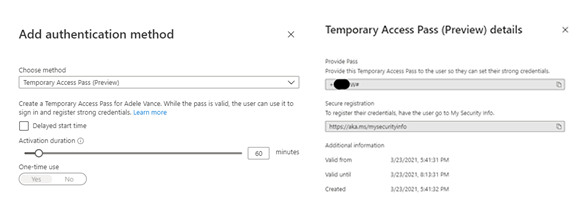
Microsoft has now made Passwordless Authentication in Azure AD generally available. Organisations can now activate Passwordless authentication and allow users to sign in using Windows Hello for Business, Microsoft Authenticator App or a compatible FIDO2 Security Key.
Along with this announcement Microsoft also released Temporary Access Pass. This feature completes the Passwordless Authentication onboarding experience. When onboarding a new user, a Temporary Access Pass, which will expire after the specified time, is provided in replacement of their password. As they setup their new device and it joins to Azure AD, they will then be asked to complete their Security Registration. At this stage they then add their Microsoft Authenticator app and utilise this to provide Passwordless Authentication to applications.
Looking for a deep dive? Check out this great Microsoft Mechanics video with Jeremy Chapman and Joy Chik.
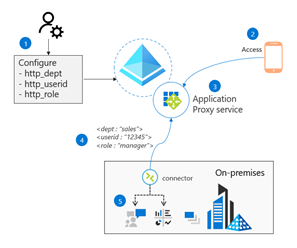
We've previously covered that Head-Based authentication was feature that had been announced in Preview and allowed organisations to publish legacy apps through the Azure AD Application Proxy and the benefits this will bring.
During Ignite 2021, Microsoft have now announced that this feature is now generally available. Organisations can now move applications that require this authentication model from third party systems like SiteMinder or Oracle Access Manager and connect them to Azure AD natively allowing organisations to consolidate their identity management infrastructure and apply more consistent Conditional Access policies to all corporate applications, whilst allowing remote workers to connect more securely.
As part of your Zero Trust approach, Verify Explicitly, you need to be able to treat access requests from your customers, partners, and vendors in the same way as those from your colleagues. Verify every request, access to data only when they need it and ensure that access is removed when it is no longer required.
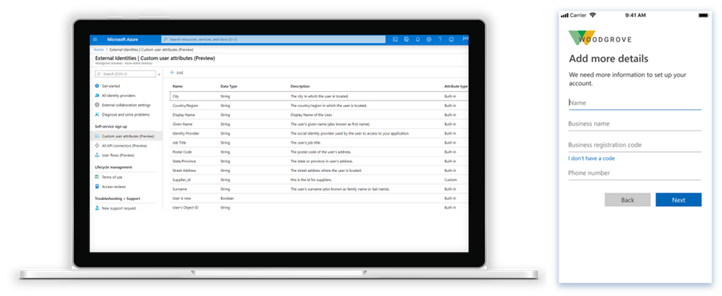
Microsoft has made Azure AD External Identities generally available this month, which brings with it the capability to secure and manage the identity and access for customers and partners. The Azure Self-Service Sign-up App makes it easy to customise the onboarding experience, whilst also being able to create and manage external users with little to no application code.
You can integrate Google and Facebook IDS and utilising the self-service sign-up gather more information about those users connecting to your apps and services.
You can read more about Azure AD External Identities at the Microsoft Azure here.
 James Parsons | Head of Modern Security
James Parsons | Head of Modern Security
Originally posted 25th March 2021